
If cyber threats are more prevalent than ever, why is cyber health still such a low priority for most clients?
Cyber risks threaten every financial asset!
Over the past two decades, cybercrime has increased 17-fold, is up more than 600% since the onset of COVID, and is expected to nearly double again over the next 3 years. As microprocessors advance and quantum computing accelerates, these trends will increase exponentially.
Aside from cyber theft, what else is at risk?
- Identity Theft
- Reputational Risk
- Physical Safety
Need we go on? Whether you’re the victim of a direct attack, malware, or poor cyber privacy practices, let’s review recommendations to ensure you’re addressing these risks.
First, let’s answer these questions. Do you:
- Use public Wi-Fi without a Virtual Private Network (VPN)?
- Leave devices (even briefly) unattended?
- Use public charging stations OR rental cars without a USB blocker?
- Leave Bluetooth on when not using it?
- Utilize smart home technology?
If you answered “yes” to at least one of these, improvement in your cyber health is possible! Whether adding technology or becoming more aware of your technology habits, let’s discuss how to create a layered digital security structure.
Tech Tools to Use Everyday
Here are the top three tech tools we recommend:
- Virtual Private Network (VPN)
- Password manager
- Private email
Create a Layered Digital Security Structure
Here are seven steps to consider:
- Install A VPN, Password Manager, and Private Email on each device.
- Populate a Password Manager with online accounts and reset passwords.
- Engage Privacy Settings on online accounts.
- Opt out of cookies.
- Engage Privacy and Security Settings on devices.
- Ensure you can wipe a device remotely.
- Prevent third-party software from automatically copying and storing passwords.
- Prevent apps from turning on the device’s microphone and camera without permission.
- Utilize Multifactor Authentication Settings
- Consider text messages a last resort!
- Engage Privacy and Security Settings on Web Browsers and Search Engines.
- Clear browsing history regularly.
- Ensure each device has up-to-date Anti-Virus Software.
Ongoing Risk Management
There are six elements to managing risk after you’ve created a layered digital security structure:
- Monitor the Dark Web and Corporate Data Breaches.
- Review Credit Reports annually.
- Be prepared to quickly address Stolen Information or Identity Theft
- Wipe Lost and Retired Equipment.
- Continuously educate yourself about evolving Cyber Risks.
- Regularly update protection if you receive a new device.
- Review your Digital Footprint annually.
This isn’t meant to scare you! But it’s essential to protect yourself BEFORE you’re the victim of cyber theft.
How do you weigh the cost vs. the benefit? Using the chart below, let’s consider the items above the line a priority before pursuing those below the line, especially if you’re just getting started.
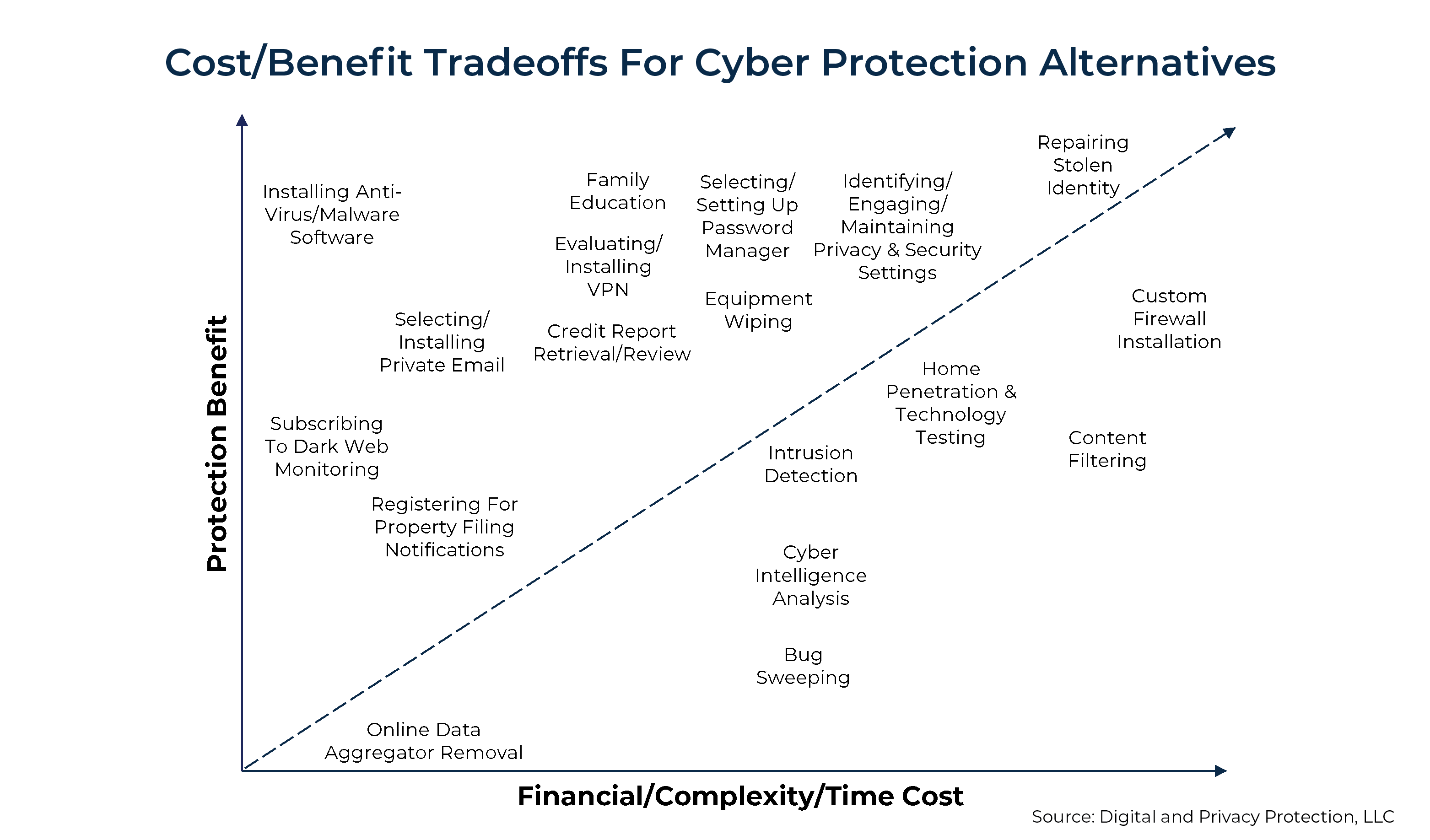
Don’t wait for the inevitable. Implementing these items may feel like a lot of work, but wouldn’t it be more work if you don’t?
Connect with us today if you want to talk through any of these items.
Please consult with your financial advisor and/or tax professional to determine the suitability of these strategies. All views, expressions, and opinions in this communication are subject to change. This communication is not an offer or solicitation to buy, hold or sell any financial instrument or investment advisory services.
